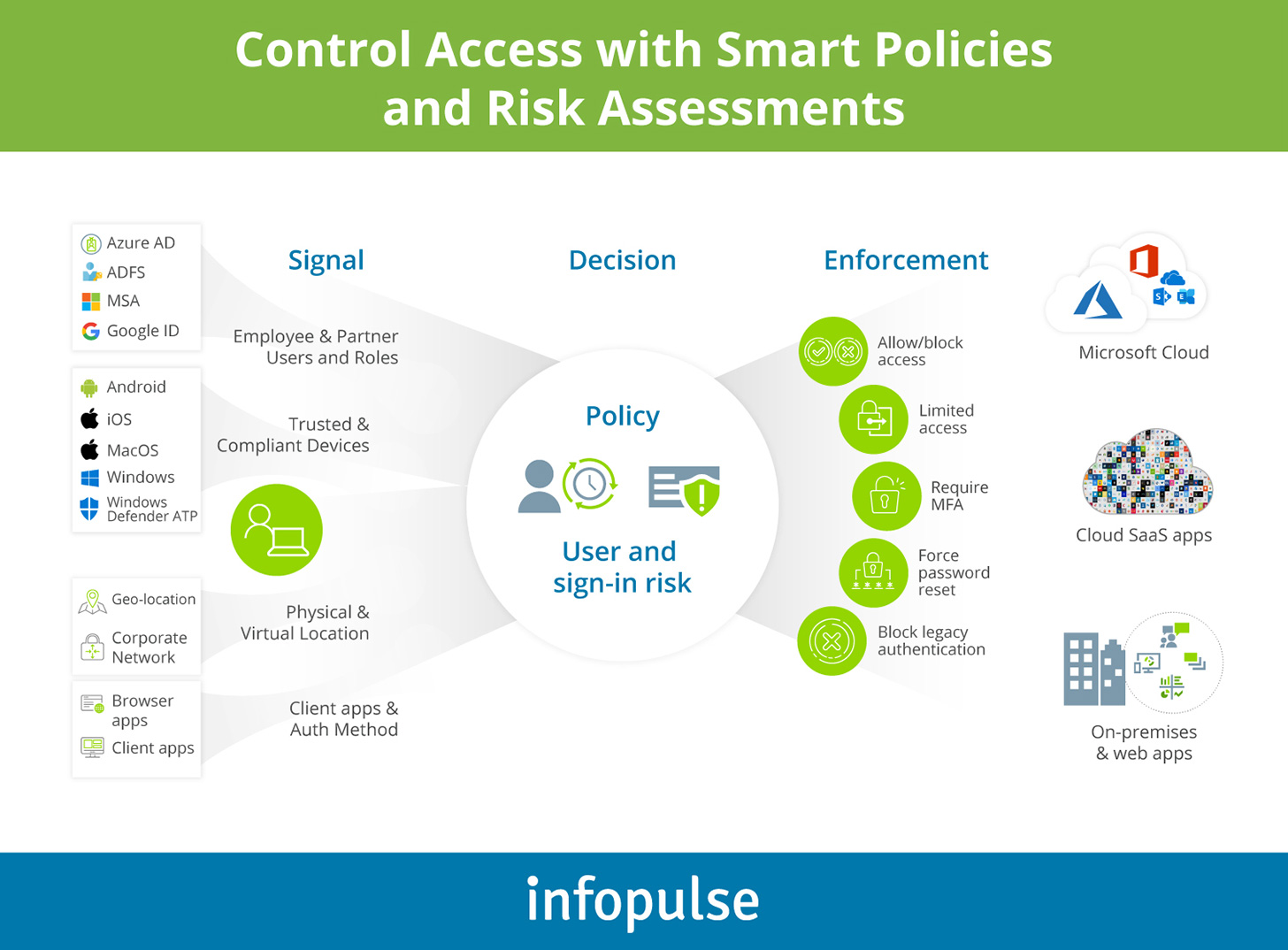
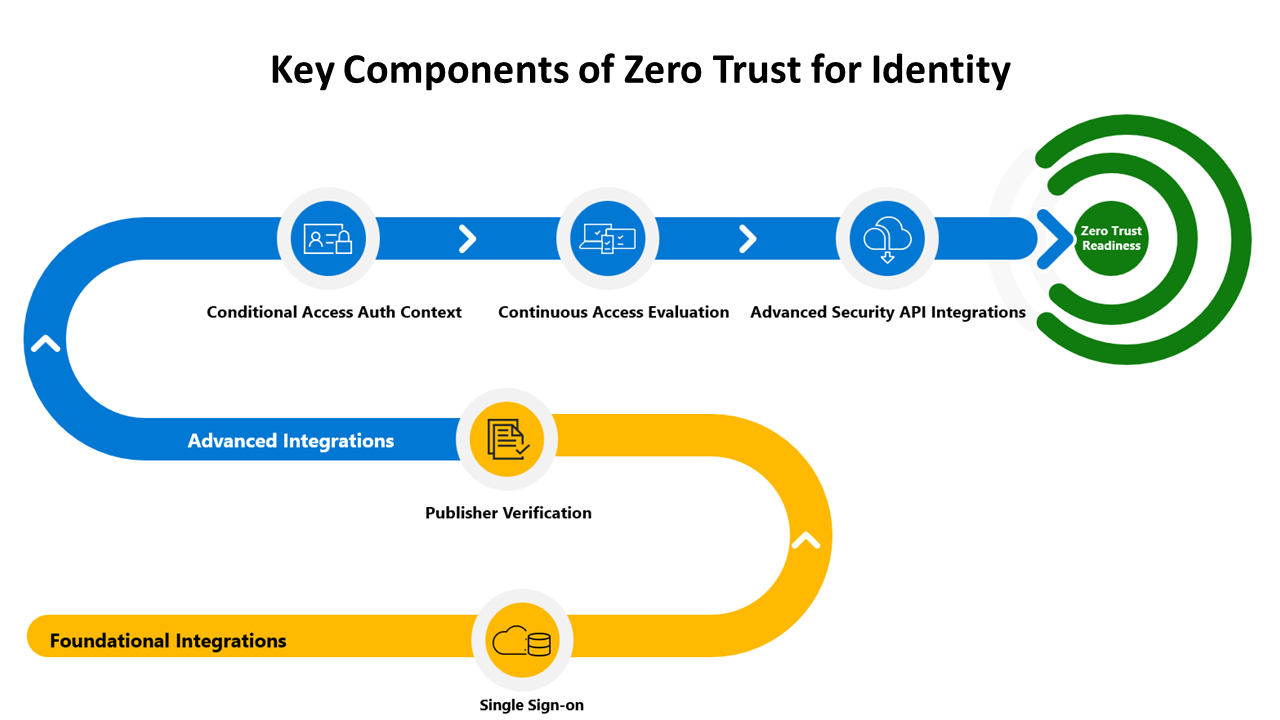
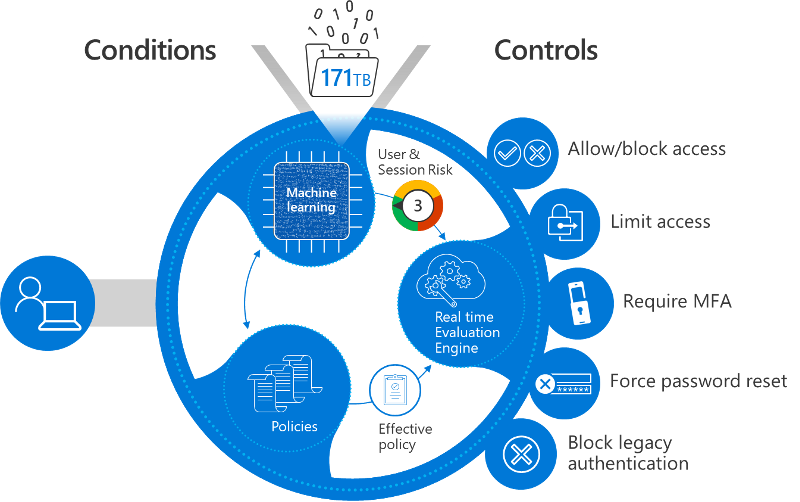
Applicare in modo esplicito il principio di verifica Zero Trust all'implementazione dell'API - Azure Architecture Center | Microsoft Learn

Zero Trust Model and Active Directory Security Tips - Microsoft Platform Management - Blogs - Quest Community

Secure AD & enable Zero Trust for security - Active Directory Management (AD Mgmt) - Blogs - One Identity Community

Building Zero Trust networks with Microsoft 365 - Malware News - Malware Analysis, News and Indicators